Space systems today underpin countless services—from global communications and navigation to weather forecasting and environmental monitoring. These platforms have become as indispensable as any terrestrial network, yet many civilian satellites and ground stations were designed long before cyber‑threats became a driving concern. As attacks on critical infrastructure grow more frequent and sophisticated, it is vital to shore up the resilience of both on‑orbit assets and their supporting ground systems.
Why Legacy Systems Are at Risk
Early civilian missions were often bound by tight schedules and modest budgets, leading engineers to focus primarily on functionality and performance. As a result, a great number of legacy platforms still run outdated operating systems, rely on unpatched communication protocols and employ hardware that cannot easily accept modern security modules. These environments were not developed under today’s secure‑by‑design paradigms—such as DevSecOps or Secure SDLC—making them vulnerable to common exploits like buffer overflows, spoofed commands or man‑in‑the‑middle attacks on data links. Moreover, inconsistencies in data formats between telemetry streams, payload imagery and system logs complicate the task of deploying uniform security updates across the mission’s lifecycle.
A Layered Risk‑Management Approach
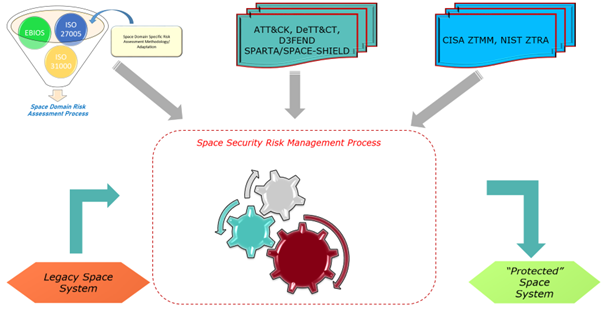
To address these challenges, the space sector can adopt a structured risk‑management process grounded in established international standards. ISO 27005 and the EBIOS method offer a practical way to catalogue mission assets—such as satellites, control centres, ground stations, and data flows—while identifying associated threats and vulnerabilities. This process supports a better understanding of where sensitive information resides and the potential operational impact of cyber incidents.
o ensure this effort is sustained over time, ISO 31000 provides a governance framework that maintains continuous oversight of risks throughout the system lifecycle—from early design and integration to operations and decommissioning. When used together, these standards can help build a common library of assets and threat scenarios that is reusable across missions and adaptable to legacy technologies.
Integrating Threat and Defence Frameworks
Standards help define the overall structure of a cybersecurity approach, but operational resilience depends on understanding how specific threats behave and how they can be countered. A number of established frameworks offer detailed support in this area. The MITRE ATT&CK framework provides a well-organized taxonomy of adversary techniques, including those that could impact ground systems or satellite control infrastructure. Complementing this, MITRE DeTT&CT helps assess whether current detection capabilities are equipped to recognize these tactics in real time. To identify appropriate mitigation strategies, the MITRE D3FEND framework offers a catalogue of defensive techniques—such as anomaly detection, endpoint hardening, or network segmentation—that can be mapped directly to known threats. In the space context, additional insight comes from sector-specific resources like SPARTA and ESA’s SPACE‑SHIELD, which focus on behaviours that are unique to orbital platforms and space communications. These include scenarios like uplink spoofing or falsified telemetry, along with proposed countermeasures tailored to the space domain. Conducting a Comprehensive Gap Analysis Putting this methodology into practice begins with a thorough inventory of all on‑orbit and ground assets, including the data flows connecting them. From there, security teams identify realistic “feared events”—for example, an unauthorized command sent to a satellite or a compromised ground‑station network intercepting downlinked telemetry. By mapping each event to existing controls—and noting where protections are missing— operators can quantify residual risk in areas like identity management, device security, network monitoring, application defences and data protection. This gap analysis then drives a prioritized roadmap, where fixes are aligned to the threats that pose the greatest danger to mission continuity and safety.
Embracing Zero Trust for Space Operations
Zero Trust principles—never trust, always verify—are a natural fit for the distributed, multi-domain environment of space missions. Guided by NIST’s Zero Trust Architecture (SP 800‑207) and the U.S. CISA Zero Trust Maturity Model (ZTMM), organizations can incrementally adopt Zero Trust by benchmarking across five pillars: Identity, Device, Network, Application, and Data. This structured approach helps space IT ecosystems transition from traditional perimeter-based defences to resilient, perimeter-less security architectures. At the data layer, Zero Trust requires end‑to‑end protections: data must be encrypted in transit, at rest, and during processing, supported by strong key management and data loss prevention (DLP) tools. To secure communications between ground segments and ground stations, the CCSDS 355.0‑B‑2 Space Data Link Security (SDLS) Protocol enforces encryption and message authentication at the data link layer. With integrated risk assessments, gap analyses, and maturity modelling, even legacy systems can be aligned with modern Zero Trust frameworks—ensuring critical space infrastructure is ready to withstand evolving cyber threats.
Conclusion
Civilian space systems designed without cybersecurity in mind now face a more hostile environment than ever before. By layering a standards‑based risk‑management process, integrating both general and space‑specific threat frameworks, and progressing along a Zero Trust maturity roadmap, operators can retrofit legacy assets to withstand modern attacks. In doing so, they will not only protect individual satellites and ground stations, but also secure the essential services on which our global economy and society depend

